Government of Canada Cyber Security Event Management Plan (GC CSEMP)
On this page
- 1. Introduction
- 2. Concept of Operations
- 3. Governance
- 4. Reporting and Communications
- Appendix A: Acronyms and Abbreviations
- Appendix B: References
- Appendix C: Detailed Roles and Responsibilities
- Appendix D: Reporting Procedures
- Appendix E: Departmental Event Impact Assessment
- Appendix F: Escalation and De-Escalation Procedures
- Appendix G: Stakeholder Placemats
1. Introduction
In this section
1.1 Context
Cyber security events related to Government of Canada (GC) information systems can have a significant impact on the delivery of government programs and services to Canadians and, consequently, confidence in government. Government security and the continuity of GC programs and services rely upon the ability of departments and agencies, as well as government as a whole, to manage cyber security events. The ability to respond to cyber security events in a consistent, coordinated and timely manner across the GC is essential to ensure the security and resilience of GC programs and service delivery.
1.2 Purpose
The purpose of this document is to provide:
- an operational framework for the management of cyber security events (including cyber threats, vulnerabilities, or security incidents) that impact or threaten to impact the GC’s ability to deliver programs and services to Canadians; and
- context for plans and procedures developed by departments and agencies to manage cyber security events related to the programs and services for which they are responsible, in alignment with this plan.Footnote 1
1.3 Scope
The scope of this plan applies to cyber security events affecting GC information systemsFootnote 2 irrespective of their categorization that:
- affect or may affect delivery of government programs and services to Canadians, government operations, security or privacy of information or confidence in government; and
- require an integrated GC-wide response to minimize impacts and enable prompt mitigation and restoration of government programs and services.
This plan also applies equally to GC information systems deemed as national security systems (NSS) (of all categorizations), with consideration of the Canadian Committee on National Security Systems CCNSS-380, Standard on Incident Management for NSS (accessible only on the GC network), and respecting the need to know nature of these sensitive information systems.
In addition, elements of this plan may be leveraged to provide a GC-wide coordinated approach for events that may arise such as:
- Security events where GC information/data hosted on non-GC information systems are or may be impacted (from a confidentiality, integrity, or availability perspective) such as a third party breach;
- Insider threat events where there is a cyber nexus; and
- Significant IT service outages affecting the GC enterprise.
This plan does not address the coordination of responses to cross-jurisdictional cyber security events (for example, with provinces, territories, municipalities, other countries or non-governmental organizations such as private sector).
1.4 Alignment with other Plans and Protocols.
This document complements other GC plans and protocols including:
- Federal Emergency Response Plan (FERP) Reference R1 – The FERP outlines the processes required to facilitate GC-wide response to severe or catastrophic events that impact the national interest and supports an all hazards arrangements and response mechanism. It also acts as an additional emergency plan that should be read in conjunction with event-specific departmental areas or areas of responsibilities's current emergency plan.
- Federal Cyber Incident Response Plan (FCIRP) – The FCIRP is a framework for the GC’s management of cyber incidents that affect assets that are not owned or operated by the GC and are essential to the health, safety, security, defence, or economic well-being of Canadians. If a cyber incident affects both GC and non-GC cyber systems, the FCIRP and the GC CSEMP will be activated concurrently (though not necessarily at the same level, depending on the severity of the respective incidents), with TBS, CCCS and PS as tripartite co-chairs.
- Significant Event Information Sharing Protocol (SEISP) (accessible only on the GC network) Reference R2 – This protocol supports the FERP and Appendix G: Mandatory Procedures for Security Event Management Control of the Directive on Security Management Reference R3.
1.5 Key Terms
The following are key definitions to support this plan:
- Compromise
-
A breach of government security. Includes but is not limited to:
- unauthorized access to, disclosure, modification, use, interruption, removal or destruction of sensitive information or assets, causing a loss of confidentiality, integrity, availability, or value;
- an event causing a loss of integrity or availability of government services or activities.
- Cybercrime
- Any crime where a cyber element (that is, the internet and information technologies such as computers, tablets or smart phones) has a substantial role in the commission of a criminal offence Reference R4.
- Cyber security
- The body of technologies, processes, practices and response and mitigation measures designed to protect electronic information and information infrastructure from mischief, unauthorized use, or disruption.
- Cyber security event
-
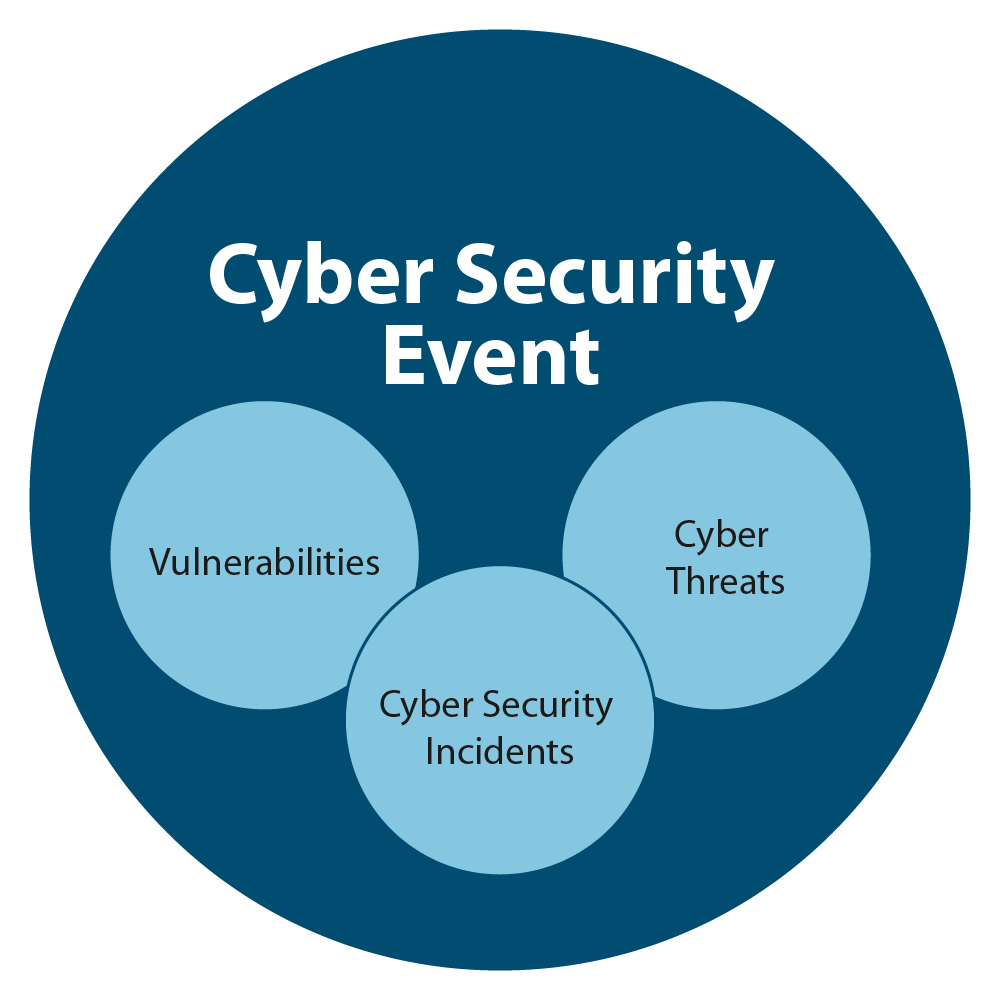
Figure 1-1: Types of cyber security events Figure 1-1 - Text version
Figure 1-1 identifies the difference between cyber security events, cyber security incidents, vulnerabilities, and cyber threats, as they are defined in the CSEMP through the use of four circles. The first larger circle represents cyber security events, and the much smaller circles within the first identifies cyber security incidents, cyber threats, and vulnerabilities as being a subset of cyber security events.
Any event, act, omission or situation that may be detrimental to government security, including threats, vulnerabilities and incidents (see Figure 1-1).
Examples of cyber security events:
- disclosure of a new vulnerability
- intelligence that a threat actor may be planning malicious cyber activities against a GC information system
- attempts to breach the network perimeter
- Suspicious or targeted emails with attachments/links that were not detected by existing security controls
- Suspicious or unauthorized network activity that represents a deviation from baseline
- Cyber security incident
-
Any event (or collection of events), act, omission or situation that has resulted in a compromise. Examples of cyber security incidents include:
- Data breaches or compromise/corruption of information
- Credential stuffing attacks
- Phishing campaigns
- Intentional or accidental introduction of malware to a network
- Denial-of-service attacks
- Web or online presence defacement or compromise (including unauthorized use of GC social media accounts)
- Successful ransomware attempts
Every cyber security incident is a cyber security event, but not every cyber security event is a cyber security incident (see Figure 1-1).
- Cyber threat
- An activity intended to compromise the security of an information system by altering the confidentiality, integrity, or availability of a system or the information it contains Reference R5.
- Privacy breach
- The improper or unauthorized access, creation, collection, use, disclosure, retention or disposition of personal information.
- Vulnerability
- Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source Reference R6 .
- Zero-day exploit
- An attack directed against a zero-day vulnerability Reference R7.
- Zero-day vulnerability
- A software vulnerability that is not yet known by the vendor, and therefore has not been mitigated Reference R7.
1.6 Application
This plan is prepared in the exercise of the responsibilities conferred to the Treasury Board of Canada Secretariat (TBS) under the Policy on Government Security (PGS) Reference R8 and is intended for all departments and agencies subject to the PGS.
1.7 Effective Date
This plan takes effect on October 27, 2023. It replaces the version dated November 10, 2022.
2. Concept of Operations
In this section
This section of the GC Cyber Security Event Management Plan (GC CSEMP) outlines the cyber security event management process, identifies implicated stakeholders, defines cyber security event response levels and escalation triggers with the aim to:
- enhance situational awareness of likely cyber threats and vulnerabilities, as well as confirmed cyber security incidents, across the GC;
- mitigate threats and vulnerabilities before a compromise can occur;
- minimize the impacts of cyber events to the confidentiality, integrity, or availability of government programs and services, information (including personal information) and operations;
- improve cyber event coordination and management within the GC, including sharing and exchange of GC knowledge and expertise;
- support GC‑wide cyber risk assessment practices and remediation prioritization efforts;
- inform decision‑making at all necessary levels; and
- enhance public confidence in the GC’s ability to manage cyber security events in a consistent, coordinated and timely fashion GC-wide.
The plan will be reviewed and tested annually, and updated if changes are warranted, to ensure effectiveness.
2.1 Process Overview
The overall cyber security event management process defined in this document has several phases, as depicted in Figure 2-1.

Figure 2-1 - Text version
Figure 2-1 represents the overall cyber security event management process and its multiple phases, as defined in this document. The four phases (preparation, detection and assessment, mitigation and recovery, and post-event activity) are depicted in the middle, with an arrow pointing from the final phase (post-event activity) back to the first (preparation) to indicate a continuous feedback loop. Under each key phase is a short description. The descriptions read as follows:
- Preparation
- Establish roles and responsibilities
- Document and test procedures
- Train personnel
- Apply protective measures
- Detection and assessment
- Monitor information sources
- Detect and recognize cyber security events
- Triage and prioritize
- Mitigation and recovery
- Conduct forensic analysis
- Mitigate (via containment and eradication)
- Restore to normal operations
- Post-event activity
- Conduct post-event analysis
- Conduct lessons learned
- Continuous improvement
Above phases 2 to 4 is a box that contains the words reporting and communication. This indicates that reporting is an ongoing activity throughout these phases. This box has arrows pointing up to a box that contains the words GC situational awareness to represent the central concept of ongoing situational awareness across the GC at every point in the event management lifecycle.
- Preparation: The initial phase involves readiness activities that departments and the broader GC should undertake to ensure they are prepared to respond to a broad range of possible cyber security events, minimizing the resultant impact.
- Detection and Assessment: The second phase involves the discovery of potential cyber security events, including emerging threats, vulnerabilities or confirmed cyber security incidents, and an initial assessment of the appropriate GC Response Levels.
- Mitigation and Recovery: The third phase consists of all response actions required by various stakeholders to minimize the impact and return to normal operations.
- Post-Event Activity: This final phase is vital for continuous improvement of the overall cyber security event management process and, as such, feeds back into the preparation phase to complete the event management life cycle.
The following subsections provide an overview of stakeholder expectations for each phase of the GC cyber security event management life cycle and will demonstrate:
- how the GC CSEMP is operationalized, in support of foundational requirements under the Policy on Government Security Reference R8 and the cyber security management function outlined under the Policy on Service and Digital Reference R9; and
- describes the key inputs and outputs from each phase. Note that in practice, phases may overlap wherein some activities from an earlier phase continue as the next phase is initiated.
All stakeholders are responsible for developing their own standard operating procedures or internal processes to deliver the expected outputs.
2.2 Preparation

Figure 2-2 - Text version
This is a repeat of figure 2-1, with all but the preparation arrow in the colour grey. The preparation arrow is highlighted in the colour blue and this image is a visual representation of the phase being described for the reader in this section.
The preparation phase is an ongoing phase in which GC organizations execute a set of continuous processes in order to ensure proactive readiness for specific or unpredictable events. It includes the development of an organizational understanding to manage cyber security risk to systems, people, assets, data, and capabilities. It also addresses the maintenance and improvement of existing capabilities and the development of new mechanisms for setting priorities, integrating multiple organizations and functions, and ensuring that the appropriate means are available to support the full spectrum of cyber security event management requirements.
The application of protective and preventive measures in advance of a cyber event is a key element of this phase. Developing and implementing appropriate safeguards to ensure delivery of critical servicesFootnote 3 including establishing repeatable and standardized processes for activities such as vulnerability management and patch management are critical in ensuring the security of systems and services. Conducting regular exercises to test both the GC CSEMP as well as departmental CSEMPs is important to ensure individual stakeholders (especially when there are changes in personnel) understand their roles, to validate the plans, and revise them based on lessons learned during exercises.
Appendix C outlines the GC CSEMP stakeholder roles and responsibilities for each phase of the GC CSEMP process.
Inputs and outputs for this phase are as follows:
| Inputs | Outputs |
|---|---|
|
|
2.3 Detection and Assessment

Figure 2-3 - Text version
This is a repeat of figure 2-1, with all but the detection and assessment arrow in the colour grey. The Detection and Assessment arrow is highlighted in the colour blue and this image is a visual representation of the phase being described for the reader in this section.
The detection and assessment phase involves the continuous monitoring of information sources for early indications of emerging cyber security events, including vulnerabilities or confirmed cyber security incidents, and the initial assessment of their impact (potential or actual) on the delivery of services to Canada, government operations or confidence in government.
Inputs and outputs for the detection and assessment phase are as follows:
| Inputs | Outputs |
|---|---|
|
|
2.3.1 Detection
The detection portion of this phase is constant for any type of cyber security event and also covers the initial notification of appropriate stakeholders. Detection occurs as a direct result of monitoring and having sufficient inputs to monitor; if the monitoring component is inadequate or incomplete, then the detection process may miss anomalies or events that could impact the GC.
2.3.1.1 Monitoring
To ensure that cyber security events are addressed in a consistent, coordinated and timely fashion GC-wide, it is essential that the Canadian Centre for Cyber Security (Cyber Centre) and TBS’s Office of the Chief Information Officer (TBS-OCIO) have up-to-date departmental cyber incident contact information to ensure the receipt of critical communications such as Cyber Centre situational awareness products and messages from the Chief Information Officer of Canada (GC CIO).
GC organizations are required to establish generic mailboxes for their departmental CIO, Designated Official for Cyber Security (DOCS), and IT Security teams, and are expected to regularly monitor them. Refer to the Guideline on Managing Cyber Incident Contact Information for more information (accessible only on the GC network).
In addition to monitoring Cyber Centre advisories, GC organizations are expected to monitor vendor notifications as part their vulnerability management programs. It is also important to note that, while it is important to leverage indicators of compromise (IoCs) (e.g., known bad IP addresses, domains, file hashes, etc.) obtained from Cyber Centre products and other threat intelligence sources to facilitate detection (and prevention) of malicious activity, there are limitations as threat actors will often change IPs, domains, reencode files, etc. to evade such defences. Therefore, establishing a robust monitoring regime and understanding baseline/normal activity will help to facilitate detection of anomalous behaviours and spot adversarial tactics, techniques, and procedures (TTPs).
Canadian Centre for Cyber Security Situational Awareness Products
Advisory (AV) - Publicly posted on the Cyber Centre website. AVs highlight vendor patches for vulnerabilities that do not meet CF or AL urgency or impact.
Alert (AL) - Publicly posted on the Cyber Centre website and disseminated through email. ALs provide a summary of the topic (incident, vulnerability, joint advisory, etc.) and technical advice. May contain additional details such as indicators of compromise (IOCs).
Cyber Flash (CF) - Non-public technical and time sensitive report. Provides detailed descriptions, detections and mitigation advice. Disseminated through email to specific distribution lists at TLP:AMBER:STRICT to ensure appropriate handling and continued sharing of cyber threat intelligence with departments.
More information on the Traffic Light Protocol (TLP) is available from the Forum of Incident Response and Security Teams (FIRST).
2.3.1.2 Reporting
GC organizations must report all cyber security incidents to the Cyber Centre, who act as the central point of contact for cyber security incident reporting for the GC. If in doubt, it is better to over report than to under report. Reporting of all events will enable the Cyber Centre to identify trends or suspicious patterns of activity and identify potential impacts to other GC organizations who may be using the same service/system as an affected department.
The Cyber Centre will ensure appropriate storage and handling of these incident reports. Information may be shared with TBS-OCIO and other LSAs, as required. To enable broader cyber defence protections, technical information such as IoCs and TTPs may be shared more widely. Sensitive department specific‑ information will not be shared beyond LSAs without approval from the department.
For cyber events affecting NSS, it is important that appropriate tools, commensurate with the security category of the affected information system, are used to securely communicate with the Cyber Centre.
Departments are expected to report incidents as per the timeframes outlined Table 2-1 .
| Type of report | Timeframe |
|---|---|
Initial incident report |
As soon as possible, and not to exceed 1 hour, after initial detection |
Detailed incident report |
Within 24 hours after detection |
Refer to Appendix D: Reporting Procedures to obtain information on how to contact the Cyber Centre, including expectations for initial and detailed incident reports.
2.3.1.3 Law Enforcement Reporting
In most cases, a cyber incident is a cybercrime. In addition to reporting to the Cyber Centre, departments and agencies are expected to report cyber incidents directly to the Police of Jurisdiction (e.g., RCMP or Military Police). It is the role of law enforcement to conduct an investigation to determine if there is reasonable evidence to suspect criminal activity, which may lead to charges, arrests, search and seizures, or other disruptive outcomes that help to deter future cyber incidents.
Refer to Appendix D: Reporting Procedures to obtain information on how to contact the RCMP.
2.3.1.4 Personal Information and Privacy Breaches
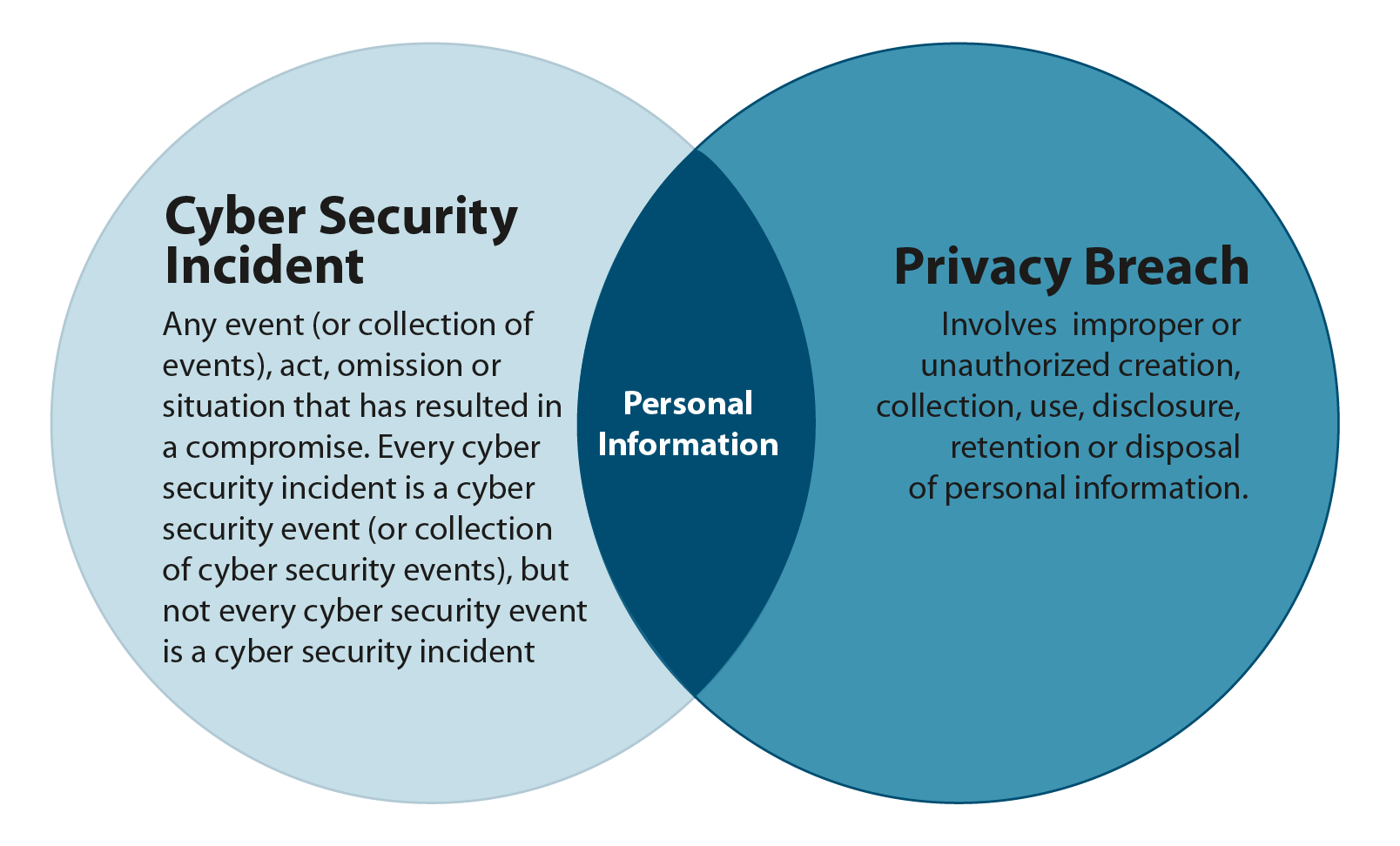
Figure 2-4 - Text version
Figure 2‑4 identifies the overlap between a cyber security incident and a privacy breach in the event that personal information may be involved. The figure uses two circles, with the circle on the left representing cyber security incidents and the circle on the right representing privacy breaches. The element of personal information represents the intersection of the two circles.
GC organizations are accountable and transparent in the protection and management of personal information.
If the possibility exists that personal information is involved in a cyber security incident, it is expected that the appropriate authorities are notified. For GC organizations subject to the Privacy Act Reference R12 and the Policy on Privacy Protection Reference R13, it is expected that the departmental Access to Information and Privacy (ATIP) offices be notified immediately to determine whether a privacy breach has occurred. If one has occurred, departments and agencies will respond in accordance with their privacy breach plans and procedures per the Directive on Privacy Practices Reference R14.
This process should involve:
- An assessment to determine the potential impact to the GC when hardware or software vulnerabilities are disclosed.
- An assessment to determine whether personal information may be involved as part of the event or incident, signaling that a privacy breach may have occurred.
- If the possibility exists that the cyber security event or incident involves personal information, departments and agencies will notify and liaise with the departmental access to information and privacy (ATIP) office. The departmental ATIP office is responsible for determining whether a privacy breach has occurred and, if so, ensuring that departmental plans and procedures for managing privacy breaches are activated.
Departments and agencies should also apprise themselves of the Directive on Privacy Practices Reference R14 and the Privacy Breach Management Toolkit Reference R15. These privacy instruments identify causes of privacy breaches, provide guidance on how to respond, contain and manage privacy breaches, delineate roles and responsibilities, and include links to relevant supporting documentation. Departments and agencies should consult legal counsel as needed.
2.3.2 Assessment
The purpose of the assessment phase is to establish a GC response level and determine whether invocation of GC CSEMP and possibly FERP governance is required. Upon detection of a cyber security event, TBS-OCIO and the Cyber Centre will conduct an initial assessment and determine the appropriate GC response through declaration of GC response level. Requisite stakeholders will then be notified of the response level and mitigation and recovery activities will follow.
2.3.2.1 GC Response Levels

Figure 2-5 - Text version
Figure 2-5 represents the four GC response levels that govern GC cyber security event management activities and dictate the necessity and degree of enterprise response required. The figure uses four stacked boxes with the level of required coordination identified to the left of the boxes.
- Level 1 – Departmental response
- Requires standard coordination
- Level 2 – Limited GC-wide response
- Requires GC CSEMP coordination
- Level 3 – Comprehensive GC-wide response
- Requires GC CSEMP coordination
- Level 4 – Emergency (crisis) response
- Requires combined FERP & GC CSEMP Coordination
There are four response levels that govern GC cyber security event management activities, as indicated in Figure 2-5. These response levels will dictate the level of coordination required in response to any given cyber security event, including level of escalation, stakeholder participation and reporting required. Table 2-2 provides more information on each of the levels.
| Level | Scope | Description | Coordination Lead |
|---|---|---|---|
1 |
Departmental Response |
Level 1 responses are limited to a departmental response. |
Department |
2 |
Limited GC-wide Response |
Level 2 indicates that Limited GC-wide coordination is required, triggering the establishment of the Event Coordination Team (ECT) (see section 3.2). At this level, all primary GC CSEMP stakeholders (and specialized stakeholders, when required) will be on heightened alert for cyber activity, monitoring GC-wide risk levels and ensuring that any potential impact is contained and mitigated. Additional targeted advice may be provided to departments and agencies on how to proceed with an event response, which could include invocation of emergency patch management processes. Events at this level will trigger invocation of TBS-SCMA’s Cyber Security Communications Framework Reference R16. GC-wide briefings will be led by GC CIO where warranted. |
ECT |
3 |
Comprehensive GC-wide Response |
Level 3 indicates that a Comprehensive GC-wide response is required triggering the establishment of the Event Management Team (EMT) (see section 3.2). At this level, event response will be fully coordinated via the ECT and EMT, with departments and agencies given ongoing direction and guidance on how to proceed with event response. Response may range from invocation of emergency patch management processes to the disconnection of systems from GC networks. Events at this level will trigger invocation of TBS-SCMA’s Cyber Security Communications Framework Reference R16. GC-wide briefings will be led by GC CIO. |
EMT |
4 |
Emergency (Crisis) Response |
Level 4 is reserved for severe or catastrophic events that affect multiple government institutions, confidence in government or other aspects of the national interest. TBS-OCIO and Cyber Centre may recommend to Public Safety the declaration of a Level 4 event, if warranted. Events that reach this level will immediately fall under the FERP governance structure, coordinated by the Government Operations Centre (GOC) in accordance with the FERP Reference R3, in order to ensure the harmonization of federal response efforts. Cyber aspects of the response in Level 4 will leverage GC CSEMP governance structures. |
PS-GOC |
2.3.2.2 Response Level Assessment
The determination of the appropriate GC CSEMP response level (Levels 2 through 3) for a cyber event will be performed jointly by TBS-OCIO and Cyber Centre, with the support of affected department(s) as appropriate. The assessment approach differs depending on whether the event is an incident or whether it is related to a cyber threat or vulnerability (see Appendix E: Departmental Event Impact Assessment for details). The response level is determined using injury to the GC (for incidents), or potential injury (for threat/vulnerability). In this assessment, several factors are considered, such as:
- likelihood of occurrence;
- exploitability or exposure of vulnerable systems;
- breadth of impact; and,
- effectiveness of security controls.
Other factors may also need to be considered, based on the context of the event in question, as depicted in Figure 2-6. While the output of this assessment guides the determination of an appropriate response level, additional factors, such as business impact and geo-political factors, may be considered by TBS-OCIO and the Cyber Centre to establish an appropriate response.
| Threats/Vulnerabilities | Incidents | |
|---|---|---|
| Level 4 Emergency Response |
|
|
| Level 3 Comprehensive GC-Wide Response |
|
|
| Level 2 Limited GC-Wide Response |
|
|
| Level 1 Departmental Response |
|
|
Any subsequent escalation or de-escalation from one level to another, as the need arises, is similarly jointly determined (see Appendix F: Escalation and De-Escalation Procedures for details).
2.4 Mitigation and Recovery

Figure 2-7 - Text version
This is a repeat of figure 2-1, with all but the mitigation and recovery arrow in the colour grey. The mitigation and recovery arrow is highlighted in the colour blue and this image is a visual representation of the phase being described for the reader in this section.
The purpose of the mitigation and recovery phase is to contain and mitigate the injury or potential injury of a cyber security event. Activities in this phase will vary depending on the nature of the event but could include actions such as the installation of patches, implementation of preventive measures, containment and eradication of a confirmed incident, the invocation of business continuity and disaster recovery plans, or the temporary shutdown of vulnerable services. Regardless of the type of event, the end goal of the phase is to minimize impacts and ensure the timely restoration of normal operations.
For incidents, containment and eradication are key components of this phase, which includes, but is not limited to, actions such as shutting down systems, disconnecting from networks or disabling functionality including accounts, addressing exploited vulnerabilities via patch installation, etc. These actions may be taken by the departmental business owners of affected assets, or as directed by their chain of command up to a department’s Deputy Head. GC organizations should document roles and responsibilities for such decisions in order to enable rapid decision making. Additionally, the GC CIO has the authority to direct a Deputy Head to undertake actions in response to a cyber eventFootnote 4.
Appendix C outlines the GC CSEMP stakeholder roles and responsibilities for each phase of the GC CSEMP process.
Inputs and outputs for this phase are as follows:
| Inputs | Outputs |
|---|---|
|
|
2.5 Post-Event Activity

Figure 2-8 - Text version
This is a repeat of figure 2-1, with all but the post-event activity and feedback arrows in the colour grey. The post-event activity and feedback arrows are highlighted in the colour blue and this image is a visual representation of the phase being described for the reader in this section.
The post-event activity phase leverages knowledge gained from each cyber security event to ensure the continual improvement of the process and, by extension, the security posture of the GC infrastructure as a whole. The purpose of this phase is to formally close out the cyber security event by conducting a post-event analysis, identifying lessons learned and driving improvements to policy, security architecture, or other controls, as required.
The degree of effort and resources allocated to this phase will vary from event to event. More complex and serious events will require deeper post-event analysis than those that are less serious in nature. Repetitive events may require post-event analysis in aggregate.
Appendix C outlines the GC CSEMP stakeholder roles and responsibilities for each phase of the GC CSEMP process.
Inputs and outputs for this phase are as follows:
| Inputs | Outputs |
|---|---|
|
|
3. Governance
In this section
3.1 Stakeholders
In addition to individual departments and agencies, which play a key role in informing and taking action on GC cyber security event management activities, a number of other stakeholders are also involved in the GC CSEMP. Below is a summary of stakeholders, organized into three major categories.
Detailed roles and responsibilities of each stakeholder are found in Appendix C: Detailed Roles and Responsibilities.
| Category | Description | Organization |
|---|---|---|
Primary Lead Security Agency (LSA) stakeholders |
Stakeholders that lead the coordination of all events that meet the criteria for a GC CSEMP Level 2 response and above. This includes potential threats, vulnerabilities, and confirmed incidents. |
|
Specialized LSA stakeholders |
Stakeholders that will be involved in the GC CSEMP process for confirmed cyber security incidents or threat events that are relevant to their specific mandate.Footnote 5 |
|
Other stakeholders |
Stakeholders who are involved in the GC cyber security event management process and may be engaged for confirmed cyber security incidents or threat events. |
|
3.2 Governance Bodies
During a cyber security event, the timely engagement of the appropriate governance bodies will focus both management and operations to prevent, detect, respond to, and recover from cyber security events in a prioritized manner. The GC CSEMP response level determines the governance bodies that are to be established. These serve to direct and facilitate mitigation and recovery activities.
Figure 3-1 depicts the relevant stakeholders for each response level and corresponding governance bodies, including:
- For Level 2 and higher events, an Event Coordination Team (ECT) is established; and
- For Level 3 events and higher, an Event Management Team (EMT) is established to provide executive level leadership (i.e., Director General (DG) level).
Ad-hoc ECT or EMT meetings may be pre-emptively stood up prior to any escalation of GC CSEMP levels as a proactive, precautionary measure and for situational awareness purposes. Escalation may or may not follow, depending on the development of an event.
Should an event be assessed at a Level 3 from the outset, governance will immediately begin at the DG level with EMT and ECT teams stood up concurrently.
Both teams, co-chaired by TBS-OCIO and the Cyber Centre, provide advice and guidance to the GC CIO. The GC CIO is responsible for executing decisions on the management of cyber security risks on behalf of the GC and directing deputy heads to implement specific response(s) to cyber security events. This includes: assessing whether there has been a privacy breach, implementing security controls, and ensuring that systems that put the Government of Canada at risk are disconnected or removed, when warrantedFootnote 6. The GC CIO is supported by the Chief Information Security Officer (GC CISO) and the Head of the Cyber Centre.
The lead minister for the response will be determined on a case-by-case basis, depending on the context of the event, supported by recommendations of the ECT, EMT, and the GC CIO.
Depending on the size and scope of the cyber event, departments directly affected by specific threats or vulnerabilities may also be invited to participate on the ECT and/or EMT. Impacted departments will always be invited to ECT and/or EMT if they are experiencing an incident. Participation will be determined by the co-chairs to ensure optimal operation of the governance bodies.
Detailed roles and responsibilities of each stakeholder, within the ECT and EMT, summarized in Table 3-2 and Table 3-3 below.

Figure 3-1 - Text version
Figure 3-1 identifies the relevant stakeholders for each of the GC response level, as outlined in figure 2-5. Figure 3-1 does not explicitly address stakeholders at Level 4 (emergency or crisis response), as Level 4 invokes FERP governance which is out of scope of this document. However, for Level 4 events, the ECT (of Level 2) and the EMT (of Level 3) remain in play to address any elements related to cyber events in the GC.
- Level 1 – Departmental response
- Stakeholders:
- Dept. CIO (or designate), supported by the DOCS)
- Departments and agencies
- RCMP
- Cyber Centre
- TBS/OCIO
- Stakeholders:
- Level 2 (and higher) – Limited GC-wide response
Event Coordination Team (ECT) is established, comprised of the following stakeholders:- Primary stakeholders:
- GC CIO (supported by the GC CISO, Deputy Chief CCCS, other GC CSEMP stakeholders as appropriate)
- TBS/OCIO (co-chair)
- Cyber Centre (co-chair)
- TBS SCMA
- Specialized stakeholders:
- PCO/S&I
- CSIS
- DND/CAF
- PS
- RCMP
- Other stakeholders:
- SSC/NSSB
- Affected department(s)
- Level 3 (and higher) – Comprehensive GC-wide response
- Primary stakeholders:
- GC CIO (supported by the GC CISO, Deputy Chief CCCS, other GC CSEMP stakeholders as appropriate)
- TBS/OCIO (co-chair)
- Cyber Centre (co-chair)
- TBS SCMA
- Specialized stakeholders:
- PCO/S&I
- CSIS
- DND/CAF
- PS
- RCMP
- Other stakeholders:
- SSC/NSSB
- Affected department(s)
- Primary stakeholders:
| Level 2 (and higher) - Event Coordination Team (EMT) | |
|---|---|
| Membership | |
| DG level (or above) stakeholders from the following departments | |
Primary LSA Stakeholders:
|
Engagement dependent on the event:
|
| Responsibilities | |
| Threats/Vulnerabilities | Incidents |
Activated by GC CSEMP Level 2 or higher.
|
Activated by GC CSEMP Level 2 or higher.
|
| Level 3 (and higher) - Event Management Team (EMT) | |
|---|---|
| Membership | |
| DG level (or above) stakeholders from the following departments | |
Primary LSA stakeholders:
|
Engagement (dependent on the event):
|
| Responsibilities | |
| Threats/Vulnerabilities | Incidents |
Activated by GC CSEMP Level 3 events or higher.
|
Activated by GC CSEMP Level 3 events or higher.
|
4. Reporting and Communications
In this section

Figure 4-1 - Text version
This is a repeat of figure 2-1, with all but the GC situational awareness and reporting and communication boxes in the colour grey. The GC situational awareness and reporting and communication boxes are highlighted in the colour blue and this image is a visual representation of the phase being described for the reader in this section.
To maintain whole-of-government situational awareness, ongoing reporting and communication between stakeholders must be maintained throughout the lifecycle of an event. This will require the engagement of additional participants from stakeholder departments and agencies to the EMT and/or ECT bodies along with bidirectional communication flows to ensure that any mitigating actions are coordinated and documented in order to minimize duplication of efforts and streamline response activities.
As per the Directive on Security Management, Appendix I: Standard on Security Event Reporting Reference R17 entrenching ongoing communication practices from detection through to the conclusion of post-event activities is imperative to ensure that mitigation advice and status updates are shared with both affected and appropriate non-affected parties in a timely fashion.
From an attribution perspective, while determining the threat actor responsible for a particular set of activities is important for cyber defence, it can be error prone. For example, many actors attempt to evade attribution through obfuscation. Therefore, it is expected that departments and agencies refrain from making any public attribution statements without engaging key GC CSEMP stakeholders such as Global Affairs Canada and/or the RCMP, as appropriate.
4.1 Reporting Structure and Communications
Figure 4-2: GC CSEMP Government-wide Reporting and Communication summarizes how reporting and communication will be handled at the government-wide level.

Figure 4-2 - Text version
Figure 4‑2 identifies the CSEMP government-wide reporting and communication, separated by the different GC response levels outlined in figure 2-5. Figure 4-2 does not describe government-wide reporting and communication at Level 4 (emergency or crisis response) invoked under FERP.
- Level 1 – Departmental response
- Cyber Centre is the central agent in gathering information
- Cyber Centre will obtain and provide information to the following sources:
- TBS/OCIO
- Departmental IT Security Teams
- Technical information sources
- TBS-OCIO is to receive information from Cyber Centre
- Level 2 – Limited GC-wide response
- Two governance bodies are identified as central sources for reporting and communication
- The first is the Event Coordination team which is comprised of the following agents:
- TBS-OCIO
- TBS/SCMA
- Cyber Centre
- Specialized LSA Stakeholders
- other CSEMP stakeholders
- The Event Coordination team will provide and receive information from the following stakeholders:
- Departmental IT Security Teams (through the Cyber Centre)
- other CSEMP stakeholders
- The EMT (through TBS-OCIO) will inform the second level of governance
- The second level of governance consists of:
- GC CIO
- Departmental CIO/CSOs
- The GC CIO will provide information to Departmental CIO/CSOs
- Level 3 – Comprehensive GC-wide response
- Two governance bodies are identified as central sources for reporting and communication
- The first is the Event Management team comprised of the following agents:
- TBS-OCIO
- TBS-SCMA
- Cyber Centre
- Specialized LSA Stakeholders
- other CSEMP stakeholders
- The Event Management team (through TBS-OCIO) will provide information to Designated Officials for Cyber Security (DOCS)
- The EMT will provide and receive information from CCNSS as a committee
- The EMT (through TBS-SCMA) will provide and receive information from Departmental Comms, PCO/Comms, and CSE/Comms
- The EMT (through TBS-OCIO) will inform the second level of governance
- The second level of governance consists of:
- GC CIO
- Departmental CIO/CSOs
- The GC CIO will provide information to Departmental CIO/CSOs
At the government-wide level, reporting and communication should adhere to the following guidelines:
- TBS-SCMA will coordinate the development of communications products and path forward in accordance with the TBS-SCMA Cyber Security Communications Framework Reference R16 in collaboration with Cyber Centre Communications, and PCO Strategic Communication (PCO SC) (for all events that require external communications or coordinated messaging (e.g. Level 3 GC CSEMP events or when warranted by Level 2 GC CSEMP events)).
- Impacted departments and agencies will develop their own stakeholder, client and public communications products, in alignment with the TBS-SCMA Cyber Security Communications Framework. In particular, TBS-SCMA and PCO SC approval is required for communications products related to Level 2 and 3 events.
- TBS-OCIO will coordinate messaging to the CIO, DOCS, and Chief Security Officer (CSO) communities, including supporting the GC CIO in GC-wide briefings, and will disseminate senior management updates as required.
- Cyber Centre will coordinate messaging to the operational (IT Security) community and disseminate technical information products (cyber flashes, advisories, alerts, and so on), including GC CSEMP response level status and situational reports (SITREPs) to implicated stakeholders as required, in collaboration with TBS and other applicable partners.
- Cyber Centre will disseminate situational reports with the GOC and Privy Council Office’s Security and Intelligence (PCO S&I), during or when considering escalation to a GC CSEMP Level 4 involving FERP.
Appendix A: Acronyms and Abbreviations
ADM |
Assistant Deputy Minister |
|---|---|
Cyber Centre |
Canadian Centre for Cyber Security, part of the Communications Security Establishment |
CCNSS |
Canadian Committee on National Security Systems |
CERT |
Cyber Event Response Team |
CIO |
Chief Information Officer |
CISO |
Chief Information Security Officer |
Comms |
Communications |
CSE |
Communications Security Establishment |
CSEMP |
Cyber Security Event Management Plan |
CSIRT |
Computer Security Incident Response Team |
CSIS |
Canadian Security Intelligence Service |
CSO |
Chief Security Officer |
DG |
Director General |
DG EMC |
Director General Emergency Management Committee |
DND-CAF |
National Defence/Canadian Armed Forces |
DOCS |
Designated Official for Cyber Security |
ECT |
Event Coordination Team |
EMC |
Emergency Management Committee |
EMT |
Event Management Team |
FERP |
Federal Emergency Response Plan |
GAC |
Global Affairs Canada |
GC |
Government of Canada |
GOC |
Government Operations Centre |
IESO |
Internal Enterprise Service Organizations |
IT |
Information technology |
IT Sec |
Information technology security |
LSA |
Lead Security Agency |
MSP |
Managed Service Providers |
SSC-ISO |
Infrastructure Security Operations, part of Shared Services Canada |
SSC-NSSB |
Network Security Services Branch, part of Shared Services Canada |
NC3 |
National Cybercrime Coordination Unit (RCMP) |
NSS |
National Security Systems |
OCIO |
Office of the Chief Information Officer, part of the Treasury Board of Canada Secretariat |
PCO |
Privy Council Office |
PS |
Public Safety Canada |
RCMP |
Royal Canadian Mounted Police |
RFA |
Request for Action |
S&I |
Security and Intelligence |
SC |
Strategic Communications |
SCMA |
Strategic Communications and Ministerial Affairs, part of the Treasury Board of Canada Secretariat |
SEISP |
Significant Event Information Sharing Protocol |
SITREP |
Situation Report |
SSC |
Shared Services Canada |
Appendix B: References
Appendix C: Detailed Roles and Responsibilities
In this section
This appendix describes roles and responsibilities of GC CSEMP stakeholders which will vary depending on the type of event (e.g. vulnerability/threat or a compromise/breach (resulting in an incident), and its priority level, in support and in the context of this plan.
C-1 Roles and Responsibilities by Organization
| Organization | Responsibilities |
|---|---|
Treasury Board of Canada Secretariat (TBS) |
TBS provides strategic oversight and direction in the GC cyber security event management processFootnote 7, ensuring that events are effectively coordinated to support decision-making and minimize potential impacts and losses to the GC. In the context of this plan, the Chief Information Officer of Canada (GC CIO) represents whole-of-government interests during cyber security events that affect or may affect the delivery of programs and services, addressing topics that include overall GC response to cyber security events and enterprise-level actions taken to protect GC information systems. This includes responsibilities for:
TBS’s Office of the Chief Information Officer (OCIO) supports the GC CIO, and provides strategic oversight responsibilities including:
In addition, TBS’s strategic communications responsibilities, via its Strategic Communications and Ministerial Affairs (SCMA) division, includes:
|
Canadian Centre for Cyber Security (Cyber Centre), part of the Communications Security Establishment (CSE) |
The Cyber Centre is housed in the Communications Security Establishment (CSE). Under the GC CSEMP, the Cyber Centre is Canada’s national coordination centre for preventing, mitigating, preparing for, responding to and recovering from cyber security eventsFootnote 9 impacting the Government of Canada. In the context of this plan, the Cyber Centre is responsible for:
|
| Organization | Responsibilities |
|---|---|
Royal Canadian Mounted Police (RCMP) |
RCMP is the lead security agency responsible for fulfilling government-wide functions related to criminal investigations.Footnote 10 In the context of this plan, the RCMP is responsible for:
|
Canadian Security Intelligence Service (CSIS) |
CSIS is mandated to investigate threats to national securityFootnote 11 including cyber-espionage, cyber-sabotage, cyber-terrorism, and cyber-based foreign-influenced activities and advise Government accordingly. In the context of this plan, CSIS is responsible for:
|
National Defence/Canadian Armed Forces (DND-CAF) |
DND-CAF is responsible for addressing cyber threats, vulnerabilities or security incidents against or on military systemsFootnote 12. In the context of this plan, DND-CAF is responsible for:
|
Public Safety Canada |
Public Safety Canada, through its National Cyber Security Directorate (NCSD), located in the National and Cyber Security Branch, leads and coordinates Canada’s national cyber security policy and strategy, and provides advice to the Minister on cyber security incidents and events affecting GC and non-GC systems. Public Safety coordinates the overall response to significant events that could affect the safety and security of Canadians. The Government Operations Centre (GOC), described in Table C-1.3, resides within Public Safety’s Emergency Management Branch. In the context of this plan, PS-NCSD is responsible for participating on CSEMP governance teams in an advice and guidance capacity. |
Global Affairs Canada (GAC) |
GAC is responsible for conducting Canada’s international relations, including working with partners and allies to address international cyber threats. In the context of this plan, GAC is responsible for:
|
| Organization | Responsibilities |
|---|---|
Shared Services Canada (SSC) |
SSC is responsible for planning, designing, building, operating, supporting, and maintaining effective, efficient and responsive enterprise IT security infrastructure services to secure Government of Canada data and systems under its responsibilityFootnote 19. This includes managing tools to support the monitoring of departmental electronic networks and devicesFootnote 20. In the context of this plan, SSC is responsible for:
|
Public Safety Canada - Government Operations Centre (GOC) |
The GOC leads and supports response coordination of any type of event affecting the national interest. It provides 24/7 monitoring and reporting, national‑level situational awareness, warning products and integrated risk assessments, as well as national‑level planning and whole‑of‑government response management. During periods of heightened response, the GOC is augmented by staff from other organizations. In the context of this plan, the GOC is responsible for:
|
Privy Council Office (PCO) |
As the hub of non-partisan advice to the Prime Minister and Cabinet, PCO helps to articulate and implement the GC’s policy agenda and to coordinate timely responses to issues facing the GC that are of national, inter-governmental and international importance. In that respect, PCO’s Security and Intelligence (S&I) team has a leading role in the coordination of government-wide response to national security emergencies. In the context of this plan, PCO Security and Intelligence (S&I) is responsible for:
In addition, PCO Strategic Communications (SC) team plays a role during significant cyber events including:
|
Canadian Committee on National Security Systems (CCNSS) |
CCNSS, co-chaired by the Cyber Centre’s Deputy Chief and the GC CIO (or delegate), develops and provides governance of an enterprise approach to National Security Systems, including establishment of an incident management plan that applies to all GC National Security Systems. In the context of this plan, CCNSS responsibilities include:
|
Director General Emergency Management Committee (DG EMC) |
The DG EMC is comprised of federal institutions with statutory mandates critical to advancing a disaster resilient Canada, as well as a broad range of federal institutions with potentially relevant mandates to emergency management. The Committee is responsible for advancing a whole-of-society perspective on horizontal emergency management issues. In the context of this plan, the DG EMC becomes the GC CSEMP interface into the FERP governance structure during Level 4 events, liaising with ADM, DM and Cabinet Committees as required. |
Departments and agencies |
Departments and agencies play a key role in GC-wide cyber security event management, whether directly affected by an event or not. Departmental governance, plans and procedures are to be developed to support departmental roles and responsibilities related to security event management and business continuity plans in place as per the Policy on Government Security Reference R8 and related directives and standards. In the context of this plan, departments and agencies, under the leadership of the departmental DOCS, in collaboration with the departmental Chief Information Officer and Chief Security Officer as appropriate, is responsible for:
|
Internal Enterprise Service Organizations (IESO) |
IESO as defined under the Policy on Government Security Reference R8 is a department or organization that provides internal enterprise services to other Government of Canada departments. IESOs are responsible for establishing mechanisms to inform service recipients of cyber security events that impact their systems or information. This includes providing service recipients with the information necessary for the completion of incident reports and responses to RFAs in a timely fashion, as well as any other digital evidence required to support departmental mitigation, recovery and post-event activities. |
External Partners |
Departments and agencies often rely on various partners external to the GC to support program and service delivery, including other orders of government and academic or scientific partners, etc. External partners are required to manage and report on cyber events in accordance with the stipulations outlined in their respective agreements with departmental service owners. |
Third-party Suppliers |
Third-party suppliers include private sector organizations such as Cloud Service Providers (CSP) and Managed Service Providers (MSP). While an MSP is a company that remotely manages IT infrastructure and user end systems on behalf of a client, a CSP dictates both the technology and the operational procedures available to the consumer (e.g. departments and agencies). Third-party suppliers are required to manage and report on cyber events in accordance with the stipulations outlined in their respective contractual agreements provisioned by departmental service owners as part of the departmental supply chain risk management approach. In the context of this plan, third party suppliers are expected to:
|
C-2 Roles and Responsibilities by Phase
This section describes roles and responsibilities of GC CSEMP stakeholders, by phase.
C-2.1 Preparation
| Stakeholder | Activities |
|---|---|
All GC CSEMP stakeholders (including all departments and agencies) |
|
Treasury Board of Canada Secretariat - Office of the Chief Information Officer |
|
Cyber Centre |
|
C-2.2 Detection and Assessment
| Stakeholder | Activities |
|---|---|
All GC CSEMP stakeholders (including Departments and Agencies) |
|
Cyber Centre |
|
Specialized LSA Stakeholders |
|
Departments and agencies |
|
Internal enterprise service organizations (such as SSC) |
|
| Stakeholder | Activities |
|---|---|
Cyber Centre |
|
Treasury Board of Canada Secretariat – Office of the Chief Information Officer |
|
Internal enterprise service organizations (such as SSC) |
|
Departments and agencies |
|
C-2.3 Mitigation and Recovery
| Stakeholder | Activities |
|---|---|
Treasury Board of Canada Secretariat – Office of the Chief Information Officer |
|
Cyber Centre |
|
Specialized LSA Stakeholders |
|
Public Safety – Government Operations Centre |
|
Departments and agencies |
|
Internal Enterprise Service Organization (such as SSC) |
|
C-2.4 Post-Event Activity
| Stakeholder | Activities |
|---|---|
Treasury Board of Canada Secretariat - Office of the Chief Information Officer |
|
Cyber Centre |
|
Internal Enterprise Service Organization (such as SSC) |
|
Public Safety - Government Operations Centre |
|
Departments and agencies |
|
All other GC CSEMP stakeholders |
|
Appendix D: Reporting Procedures
In this section
The following section outlines the procedures for reporting to the Cyber Centre or the RCMP. Examples of types of events that should be reported include, but are not limited to:
- Suspected or actual compromise of any administrative credentials
- suspicious activity on devices that have been in foreign countries or have been connected to untrusted networks or devices (e.g., a USB key gift)
- suspicious or targeted emails with attachments or links that were not detected by existing security controls
- suspicious or unauthorized network activity that represents a deviation from baseline
- data breaches or compromise or corruption of information
- intentional or accidental introduction of malware to a network
- denial of service attacks
- successful ransomware attempts
- web or online presence defacement or compromise (including unauthorized use of GC social media accounts)
For cyber security incidents involving NSS, only submit high level details when contacting the Cyber Center or Police of Jurisdiction (e.g., RCMP or Military Police) and provide further details over appropriate secure channels.
D-1 Incident Reporting Information
Table D-1 outlines the information that should be provided when reporting an incident to the Cyber Centre or the RCMP.
To balance timeliness with completeness of reporting, departments are expected to:
- provide an initial report as soon as possible, and not to exceed 1 hour, after initial detection with as much information as possible; and
- provide a more complete, detailed report within 24hrs after detection, addressing the remaining items in Table D-1 (to the greatest extent possible).
| ID | Type | Description |
|---|---|---|
1 |
Contact Details |
Name, Phone #, Email, Organization/Department, and Role |
2 |
Type of Request |
Request for Assistance (Urgent / Not Urgent) or Information Only. |
3 |
Incident Description/Summary |
Description of the cyber incident by answering as many of the following questions as possible
|
4 |
Additional Information |
Any further information including references, device details, indicators such as URLs, IP addresses, any mitigation actions taken, etc. |
D-2 How to Contact the Cyber Centre
Regular reporting channels should be used to contact the Cyber Centre in the case of an incident. If no regular reporting channels have been established, Government of Canada organizations can use the Cyber Centre’s Incident Reporting Portal. Upon receipt, the Cyber Centre will triage and provide a response in a timely manner.
D-3 How to Contact the RCMP
To report a cybercrime incident to the RCMP, departmental representatives should contact the NC3 at NC3Cyber-CyberGNC3@rcmp-grc.gc.ca or contact the RCMP Operational Coordination Centre (OCC) and request to speak to someone at the NC3.
Upon receipt of the report of the incident, the RCMP will triage and provide a response in a timely manner. Responses from the RCMP may include an email response advising of the receipt of the report, a request for further information and / or a request for a virtual or in-person interview.
Appendix E: Departmental Event Impact Assessment
In this section
The purpose of this Appendix is to outline a high-level process that could be used to assess impact related to a cyber security event. This two-step process can be adopted and leveraged by Departments as required to inform their incident response plan.
Step 1: Injury Test
Assessment of impact for all cyber security events (threats, vulnerabilities and confirmed incidents) begins with an injury test to measure the degree of injury that could reasonably be expected to occur due to a compromise, resulting in an incident
Step 2: Risk Assessment
For cyber threat and vulnerability events, determine the probability of injury occurrence to obtain a more accurate representation of potential departmental impact
E-1 Step 1: Injury Test – for all cyber security events
The injury test, performed using Table E-1 , is based on severity and scope of the injury that could be reasonably expected to occur.
Severity
The severity levels can be characterized as
- Limited: an event that, if it occurred, would cause limited injury.
- Serious: an event that, if it occurred, would cause serious injury.
- Severe: an event that, if it occurred, would cause severe injury.
The severity of the injury refers to the level of harm, damage, or loss for the following types of injury:
- harm to the health and safety of individuals
- financial losses or economic hardship
- impacts to government programs and services
- loss of civil order or national sovereignty
- damage to reputations or relationships
- injury to the nation or national security
Other factors specific to a departmental or agency mandate or operational context may also be considered as well as the security categorization of the information system as defined by the Directive on Security Management, Appendix J: Standard on Security Categorization Reference R18 .
Scope
The scope of injury refers to the number of people, organizations, facilities or systems impacted, the geographical area affected (for example, localized or widespread), or duration of the injury (for example, short term or long term). The scope of injury can be characterized as:
- Wide: widespread; national or international; multiple countries or jurisdictions; major government programs or sectors
- Medium: jurisdiction, business sector, government program; group or community
- Narrow: individual, small business
| Scope | ||||
|---|---|---|---|---|
| Narrow | Medium | Wide | ||
| Severity | Severe | Medium | High | Very high |
| Serious | Low | Medium | High | |
| Limited | Low | Low | Medium | |
| Result | Departmental impact level | |||
Table E-2 can be consulted to analyze potential expected results of a compromise and validate the outcome of the initial injury test. Once confirmed, this value can be entered in the incident report and submitted to the Cyber Centre.
| Impact | Result of compromise |
|---|---|
Very high |
|
High |
|
Medium |
|
Low |
|
E-2 Step 2: Risk assessment – for cyber threat and vulnerability events only
Unlike cyber security incidents, where injury has been realized, injury is still in a potential state for cyber threat and vulnerability events. In order to establish an accurate potential impact level, a risk assessment is expected to be conducted (using Table E-3 ) to determine the probability of occurrence for the injury. Using the results of the injury test performed in Step 1, a risk-modified departmental impact level is determined based on factors such as intelligence indicators (likelihood of compromise), exploitability, exposure of affected information systems, and implementation of compensating controls.
| Exposure | |||||
|---|---|---|---|---|---|
| Low | Medium | High | Very high | ||
|
|
|
|
||
| Impact level (as per injury test in Step 1) | Very high | High | High | High | Very high |
| High | Medium | Medium | High | High | |
| Medium | Low | Medium | Medium | Medium | |
| Low | Low | Low | Low | Low | |
| Result | Risk modified departmental impact level | ||||
This risk-modified departmental impact level is to be reported to the Cyber Centre (when requested via an RFA) for consumption at the GC-wide level.
Cyber threat or vulnerability events are to be classified as cyber security incidents as soon as injury is realized. When injury moves from a potential state to a realized state, the injury tests in this appendix will require re-evaluation and resubmission to the Cyber Centre to determine whether changes to event response or further escalation are required.
Appendix F: Escalation and De-Escalation Procedures
In this section
F-1 Escalation Procedures
Table F-1 outlines the activities for escalation procedures between GC CSEMP response levels.
| Escalation Procedures | Activities |
|---|---|
Escalation from a Level 1 to a Level 2 GC CSEMP Event |
|
Escalation from a Level 2 to a Level 3 GC CSEMP Event |
|
Escalation from a Level 3 to a Level 4 GC CSEMP Event |
|
F-2 De-escalation Procedures
GC response levels can be downgraded as a cyber event unfolds. Several de-escalating factors will need to be considered including if: an incident is sufficiently contained or determined to be less severe than originally determined; or the threat is reduced, or vulnerability mitigated. Table F-2 outlines the activities for de-escalation procedures between GC CSEMP response levels.
| Escalation Procedures | Activities |
|---|---|
De-escalation from a Level 4 to a Level 3 GC CSEMP Event |
|
De-escalation from a Level 3 to a Level 2 GC CSEMP Event |
|
De-escalation from a Level 2 to a Level 1 GC CSEMP Event |
|
Appendix G: Stakeholder Placemats
This resource is only accessible on the internal GC network. A copy of the placemat is available on the GC Cyber Security gcXchange Community page, under Cyber Security Event Management Resources.
Page details
- Date modified: